JS Business Solutions Blog
As a general rule, necessity dictates when a business upgrades the technology, they use each day. Sometimes it is because the tech they have been using can no longer support their needs, and sometimes, the solutions that are utilized simply aren’t efficient enough to keep up with operations any longer. New technologies may be adopted as a means to increase productivity, while others may actually be required by government-mandated regulations.
Businesses deal in relationships. They have to create a relationship with their clients and customers to keep them coming in the door, whether they are serving other business needs or consumer ones. Of course, it can be hard enough to manage all of the relationships in one’s personal life… how can one possibly add business relationships into the mix?
The Internet is an indispensable tool, that much is certain. Unfortunately, the only other certainty is that there are millions of people on the Internet looking to intercept data, breach networks, and steal anything they can. That is why your business spends those extra precious dollars on cybersecurity. One tool that isn’t always mentioned as a part of a cybersecurity strategy is the virtual private network, or VPN.
With the big day just over a week away, a lot of people are scouring websites for the right gift. While frantic online shopping like this has become a holiday tradition in its own right, there is no reason to spoil the season by having your identity stolen online. That’s why we wanted to quickly review a few safeguards to keep in mind while online shopping.
There are plenty of reasons - including employee satisfaction, productivity benefits, and cost savings, to boot - that many organizations have adopted BYOD (or Bring Your Own Device) policies. Having said that, it is important that you have a few guidelines and other policies firmly established concerning your employees’ secure use of their own devices… policies, such as:
To keep your business’ network and infrastructure secure, you need to adhere to solid password practices. That includes not using the same password across different sites, using password managers when possible, and choosing passwords that are unique, but memorable. One of the most useful technologies used to secure accounts is two-factor authentication (2FA). Let’s take a look at how to incorporate 2FA into your security strategy.
In today’s day and age, it is effectively unheard of for a business not to rely on the Internet in some shape or form. This means that maintaining a well-functioning network is of increased importance for businesses of all sizes, which in turn will require you to make a few critical determinations. Here, we’ll examine some of the factors that may indicate your networking equipment is due for a refresh.
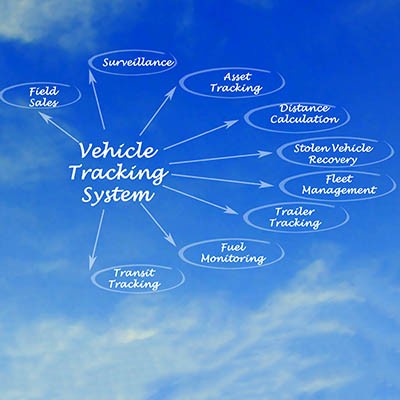
The Internet has made it possible to purchase goods and services so easily that we need new people to blame when we don’t have those purchases in hand in less than 72 hours. The speed in which shipping is capable nowadays is the result of superior logistics. If your business is beginning to utilize ecommerce, or if it has trouble with the costs associated with the distribution of your goods, a fleet management system could be the solution to your problems.
Employees are without a doubt the most unpredictable resource within your business. Nothing can be more catastrophic to data security than a careless or untrained worker. Enforcing safe practices and policies doesn’t have to feel like a chore, if training is handled properly. In fact, employees typically become eager to learn how to avoid the latest and greatest cyber-related threats. These threats plague not just our work lives, but our everyday lives as well. Today, we will discuss what you and your employees should be aware of in today’s connected world.
Regardless of what you do, it’s a good bet that your business creates a lot of data. Some of which is completely essential to its sustainability. In order to protect it against data loss and disaster, you will need data backup. Today’s best options leverage cloud computing to ensure redundancy and availability. Today, we’ll take a look at data backup and how choosing one that incorporates cloud services can actually save your business.
Ever since it started to be looked on as a reliable computing option for businesses, cloud computing has been exceedingly popular. Businesses and individuals use cloud computing platforms for their infrastructure needs, their application deployment, their file sharing and storage, and for redundancy to protect their business, but have you ever wondered how the cloud platforms themselves are kept up to date? Today, we will look into it.
Many business owners like to crunch the numbers in order to fully understand where their hard-earned money is going. Essential business communication tools are just one of the things that are under your expense's category. However, phone service is dwindling across the globe, much in part due to the benefits associated with VoIP, or Voice over Internet Protocol.
Most of us have a love-hate relationship with social media. A particularly controversial platform we discuss quite a bit on our blog is Facebook. Privacy is a monumental concern in the digital age, so today we thought we would go over settings you might not even realize are enabled on your Facebook profile.
If you haven’t read part one of our Facebook privacy blog, it wouldn’t hurt for you to go back and read that one first. Today, we will be building off of that blog, teaching people how to properly configure their accounts to give them the best chance to lock down their private information.
Of course, Facebook, being one of the predominant web-based services in the world, has a checkered history when it pertains to individual’s privacy. In fact, I think a fair share of its ongoing troubles when it comes to individual privacy have a lot to do with their overwhelming success.
Would you consider Facebook to be popular? It’s an interesting question. It’s like asking people if they think McDonalds is popular. These days Facebook is used by one in every four people in the world, yet there are very few people that will actively come to the social media giant’s defense, let alone admit to spending nearly half of their time online on the site (either via an Internet browser or via an app).
While most businesses need the same basic technology to support their operations, some industries have additional, more specific needs that require a more specialized tool to accomplish. As we leave this series behind, let’s briefly consider how a managed service provider can be a valuable resource for a business operating in one of these industries.
Modern businesses can now make use of increasingly powerful technology solutions… as long as they have a means of obtaining and incorporating these solutions into their operations. The services that a managed service provider can deliver include procurement assistance. To wrap up our series on the value that managed services can provide, let’s discuss this aspect.
Your business’ data is a key component to its success, and with a managed service provider on your side, it becomes even more beneficial for you to put to use. As we carry on with our series describing the value of a relationship with a managed service provider, we’ll look at a few ways that your business can benefit from the data services that this relationship can provide.